# Defence In Depth
#cyber-security #cloud-security
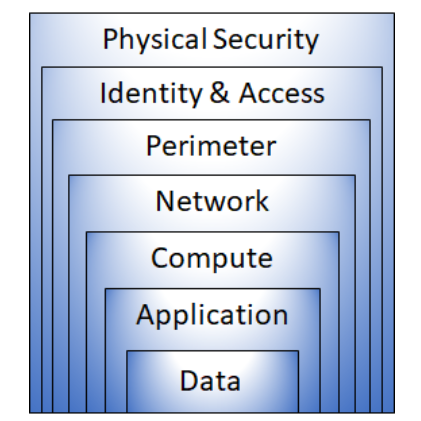
Defense in depth uses a layered approach to security, rather than relying on a single perimeter. A defense in-depth strategy uses a series of mechanisms to slow the advance of an attack. Each layer provides protection so that, if one layer is breached, a subsequent layer will prevent an attacker getting unauthorized access to data.
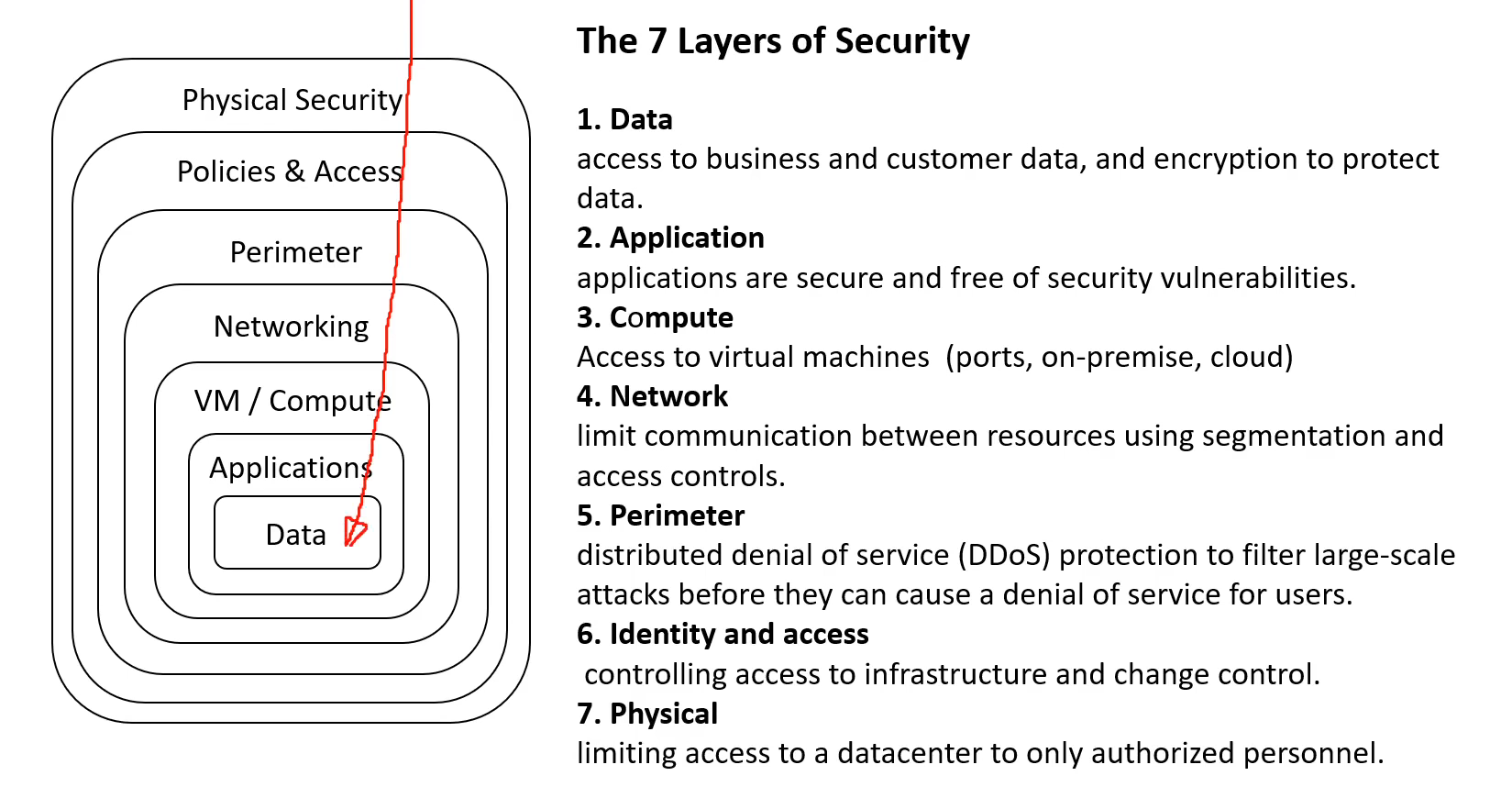
Example layers of security might include:
- Physical security such as limiting access to a datacenter to only authorized personnel.
- Identity and access security controls, such as multifactor authentication or condition-based access, to control access to infrastructure and change control.
- Perimeter security of your corporate network includes distributed denial of service (DDoS) protection to filter large-scale attacks before they can cause a denial of service for users.
- Network security, such as network segmentation and network access controls, to limit communication between resources.
- Compute layer security such as securing access to virtual machines either on-premises or in the cloud by closing certain ports.
- Application layer security to ensure applications are secure and free of security vulnerabilities.
- Data layer security including controls to manage access to business and customer data and encryption to protect data.