# Encryption
#cyber-security #security #encryption
Encryption is the process of making data unreadable and unusable to unauthorized viewers by using of a secret key to access the data. This ensures safety of information and sensitive information.
There are two types of encryption strategies.
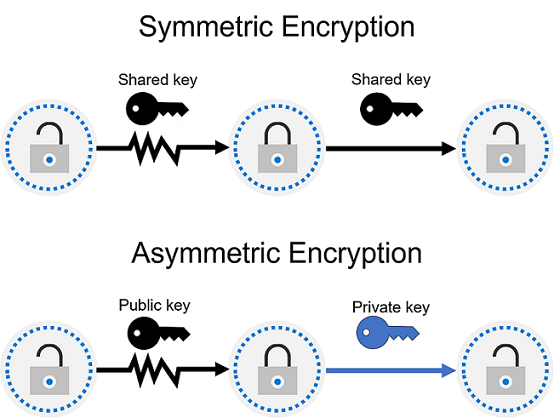
Symmetric uses the same key to encrypt and decrypt the data.
Asymmetric uses a public key and private key pair. Either key can encrypt data, but a single key can’t be used to decrypt encrypted data. To decrypt, you need a paired key. Asymmetric encryption is used for things such accessing sites on the internet using the HTTPS protocol and electronic data signing solutions. Encryption may protect data at rest, or in transit.